Security Settings¶
Based on security requirement, system administrator can configure password rules for all internal account users and login security settings for all users.
Setting Password Rules¶
System administrator can configure password rules for all internal account users by the following steps:
Log in the Admin Console of Application Portal, and select Security Settings from the navigation bar.
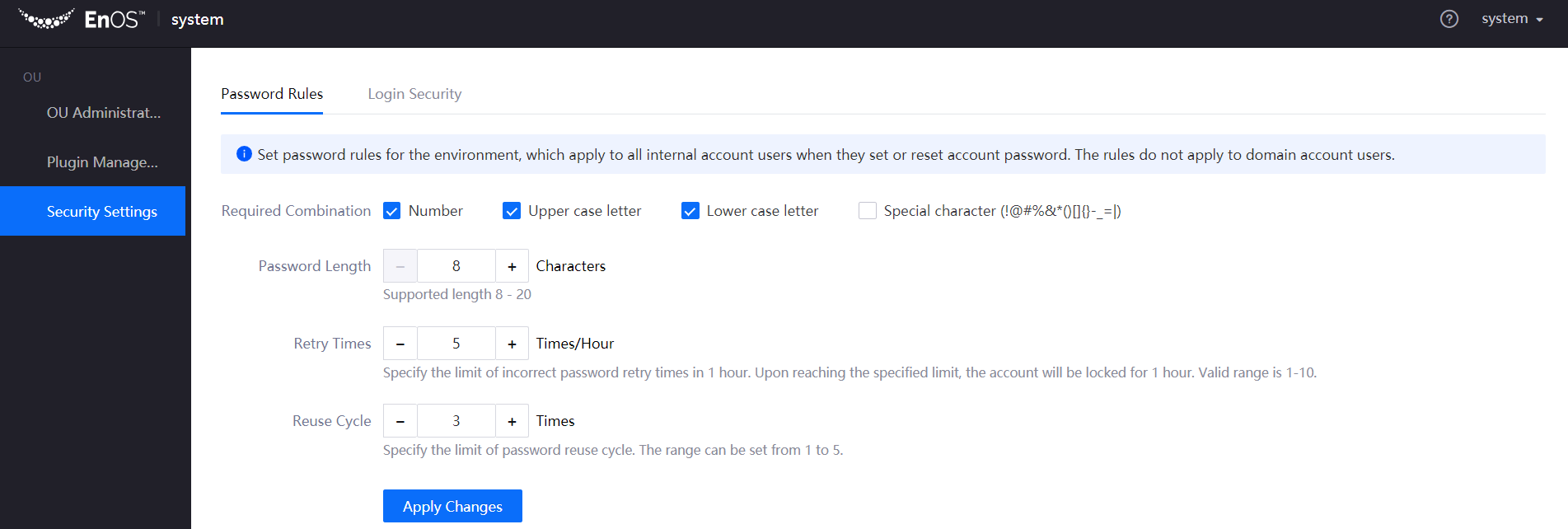
Under the Password Rules tab, complete the following password rule configuration:
Select the required combination for password: number, upper/lower case letters, and special characters.
Specify password length. Valid range is 8-20 characters.
Specify the limit of incorrect password retry times in 1 hour. Upon reaching the specified limit, the account will be locked for 1 hour. Valid range is 1-10 times.
Specify the limit of password reuse cycle. The range can be set from 1 to 5.
Click Apply Changes to complete the settings.
Note
After the password rule settings take effect, all internal users in the environment must comply with the rules when they set or reset account password. The rules do not apply to domain account users.
Setting Login Security Rules¶
System administrator can configure login security rules for all users in the environment by the following steps:
Log in the Admin Console of Application Portal, and select Security Settings from the navigation bar.
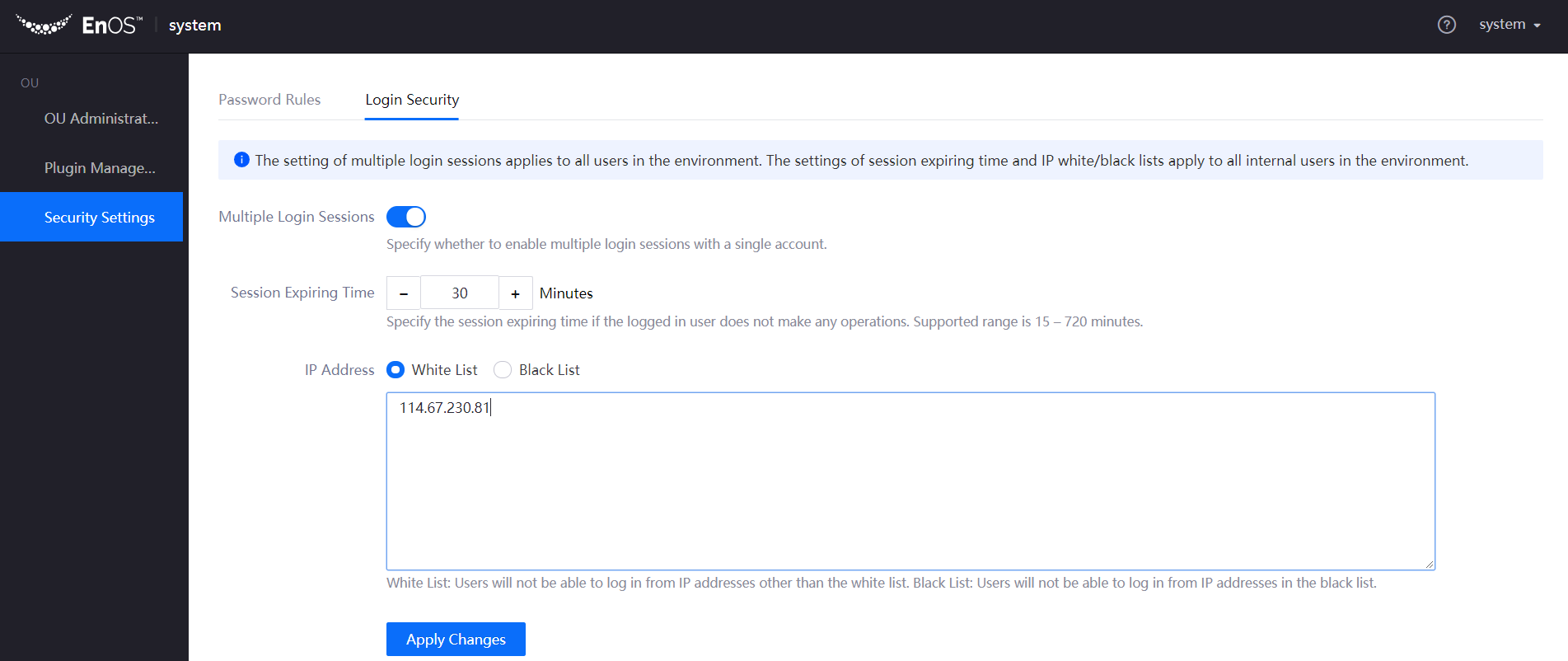
Under the Login Security tab, complete the following account login rule configuration:
Specify whether to enable multiple login sessions with a single account.
Specify the session expiring time if the logged in user does not make any operations. Supported range is 15 – 720 minutes.
Set IP white list or black list.
Click Apply Changes to complete the settings.
Note
The setting of multiple login sessions applies to all users in the environment. The settings of session expiring time and IP white/black lists apply to all internal users in the environment.