Device Security Schemes¶
To ensure the security of the devices and data transmission, the device needs to be authenticated before exchanging data with the EnOS IoT Hub. EnOS supports the following authentication methods:
Secret-based one-way authentication
Certificate-based two-way authentication
Authentication Process¶
Smart Device Authentication¶
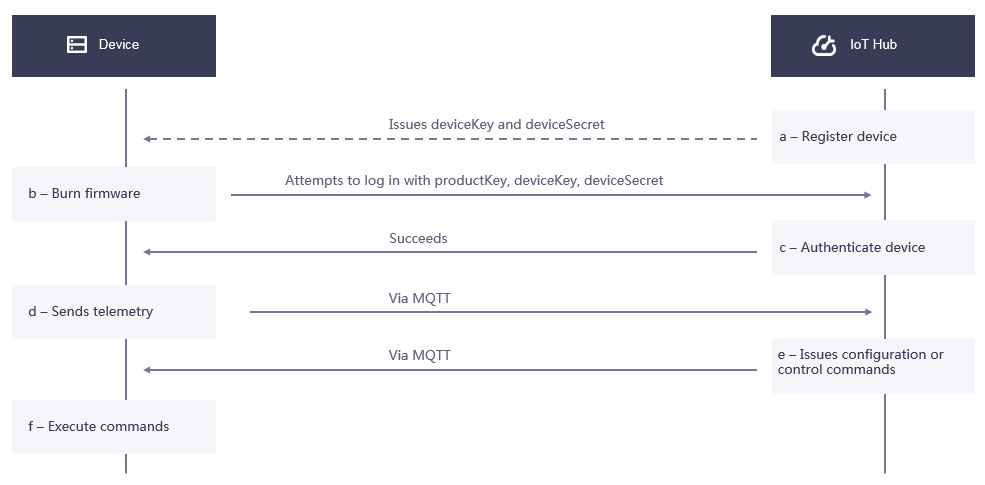
Log in to the EnOS Management Console and create the model, product, and device for the device to be onboarded.
Configure the information required for authentication for the device.
Activate the device and try to connect to EnOS using the configured authentication information. If the device is authenticated, it will successfully connect to EnOS, otherwise the connection will fail.
Non-smart Device Authentication¶
Log in to the EnOS Management Console and create the model, product, and device for both the device and the proxy gateway device to be onboarded.
Configure the authentication information required for onboarding the device on the gateway device.
Activate the gateway device and try to connect to EnOS using the configured authentication information. If the device is authenticated, it will successfully connect to EnOS, otherwise the connection will fail.
Secret-based One-way Authentication¶
Secret-based one-way authentication uses the following authentication key pairs.
Product authentication pair:
product keyandproduct secret.Product key: The global unique identifier issued by EnOS to the product. It can be found at Device Management > Products > Product Details.Product secret: The product secret issued by EnOS, which is paired withproduct key. It is used for the dynamic activation of devices. To initiate the dynamic activation, a device sends a request containing theproduct key,product secret, anddevice keyto EnOS to get thedevice secretupon its first connection to EnOS. It can be found at Device Management > Products > Product Details.
Device authentication pair:
device keyanddevice secret.Device key: A globally unique device identifier that is user-defined or auto-generated when a user registers (creates) a device on EnOS. It can be found at Device Management > Device Assets > Device Details.Device secret: The device secret issued by EnOS, which is paired withdevice key. It can be found at Device Management > Device Assets > Device Details.
The secret-based one-way authentication (static authentication) is the default authentication method for EnOS.
Device Authentication Operations¶
Perform the following operations in the following order to connect a device to EnOS.
Registration
Create a device instance in EnOS by either using the EnOS Management Console or calling an API. The device will be in an Inactive state.
When using the EnOS Management Console to register a device, you need to create the model, create the product, and register the device in sequence.
When calling an API to register a device, you can also call an API to create the product and create the device, but the creation of models still need to be done in the EnOS Management Console.
Authentication
You can either dynamically or statically authenticate a device. Once the device is authenticated, its state changes from Inactive to Online. If an Online device does not send any data to EnOS within the specified time range, it will become Offline.
Device Authentication Mode and Device States¶
The state of a device when it is first registered before authentication is inactive. You can dynamically or statically activate the device.
Dynamic Authentication¶
To use dynamic authentication, go to Device Management > Products. Find the product that the device is created from and click its View icon. In the Basic Information tab page, enable the Enable Dynamic Activation switch. The process of dynamic authentication is as follows:
After being created on EnOS, the device sends a request carrying the
product key,product secret, anddevice keyfor thedevice secret. If the authentication is successful, adevice secretneeded for subsequent communication will be returned to the device, and its status will change from Inactive to Online. The device will then be able to send data to EnOS. If no data is sent within a certain period of time, the status of the device will change to Offline.As long as the device status is inactive, the
device secretcan be obtained repeatedly using theproduct key,product secret, anddevice key.If the device is Online or Offline, and requires re-authentication, first delete the device instance in Device Management > Device Assets, re-create a device instance, and then use the new instance’s
product key,product secret, anddevice keyto get thedevice secret.
After the first successful authentication, the
product key,device key, anddevice secretwill be used for subsequent authentications.
Static Authentication¶
This is the default authentication method. The process of static authentication is as follows:
The device sends an authentication request carrying the
product key,device key, anddevice secret. These three parameters can be retrieved from Device Management > Device Assets > Device Details after creating a device in the EnOS Management Console. You need to configure these three parameters on the device side.Once the device is successfully authenticated, its status will change from Inactive to Online. The device will now be able to communicate with EnOS. If no data is sent within a certain period of time, the status of the device will be changed to Offline.
Note
When the device is not working properly or you do not want to receive its data, you can disable it by toggling its Enable/Disable switch in Device Management > Device Assets. The device will then go offline and its status will change to Disabled.
Certificate-based Two-way Authentication¶
The certificate-based authentication refers to device identity authentication with authentication keys. It is a two-way authentication mechanism, that is, the IoT Hub validates the identity of the device and the device verifies the identity of the IoT Hub. To enforce two-way authentication, the certificate-based authentication mechanism can be used.
To enable certificate-based authentication, log in to the EnOS Management Console, go to Device Management > Products > Product Details, and enable Certificate-Based Authentication.
When certificate-based authentication is enabled, EnOS enforces the following security schemes to secure the connection between the EnOS Edge and EnOS IoT Hub.
The communication between the EnOS Edge and EnOS IoT Hub is based on certificate-based bi-directional authentication.
Supports the RSA algorithm to verify the signature and uses a 2048-bit RSA key.
Best Practices¶
If the two-way certificate-based authentication method is enabled, we recommend the following best practices.
Provide a unique certificate for each device to allow for granular management such as certificate revocation.
The device must support certificate replacement to ensure smooth operation when the certificate expires.
Setup Phase¶
The following diagram illustrates the process of secure communication between the edge and EnOS cloud based on X.509 certificate. You can also use gateway devices other than EnOS Edge.
EnOS Cloud Acquires X.509 Certificate¶
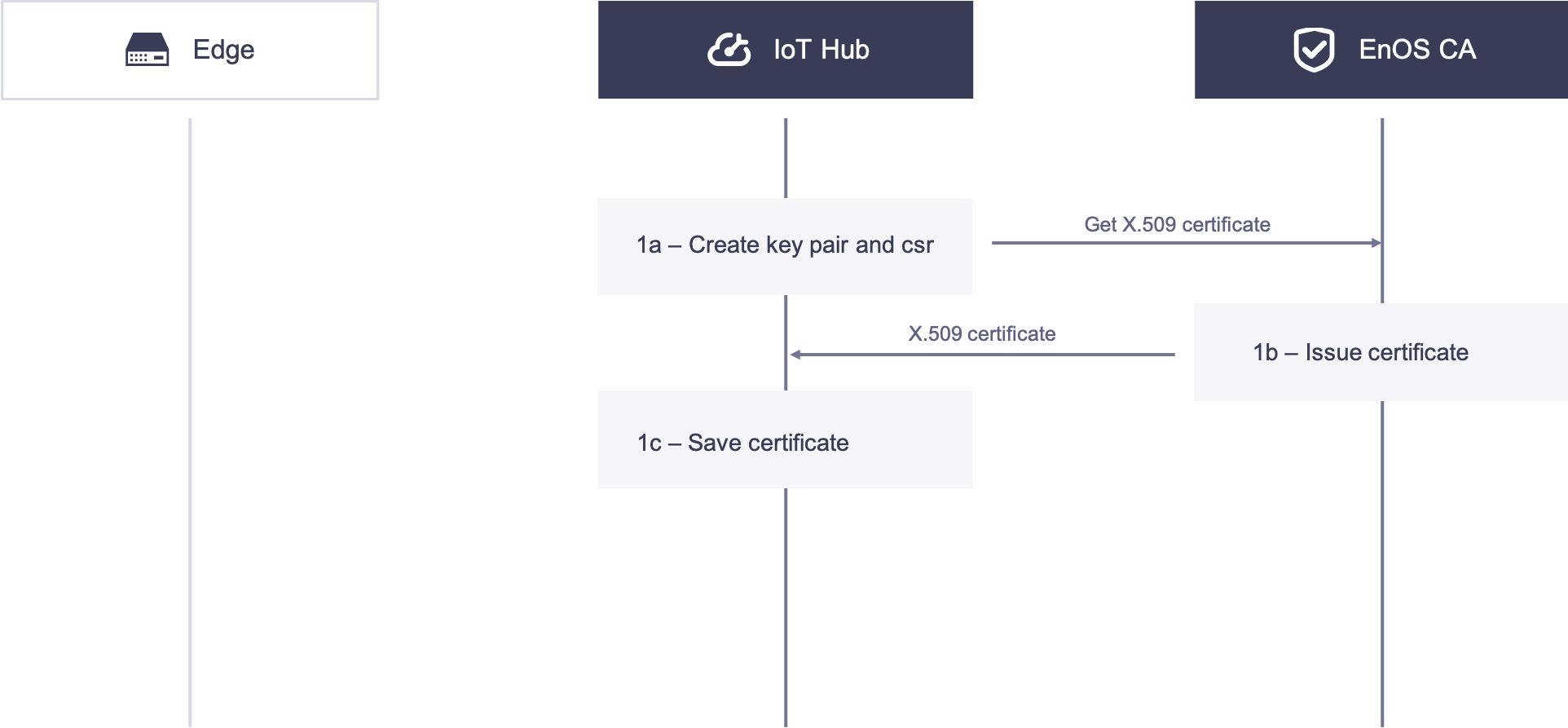
1a. EnOS Cloud the creates authentication keys and CSR locally, and acquires the X.509 certificate with the CSR by calling the X.509 certificate service API.
1b. The CA issues the X.509 certificate and sends the certificate to EnOS Cloud.
1c. EnOS Cloud receives and stores the X.509 certificate.
Edge Acquires X.509 Certificate¶
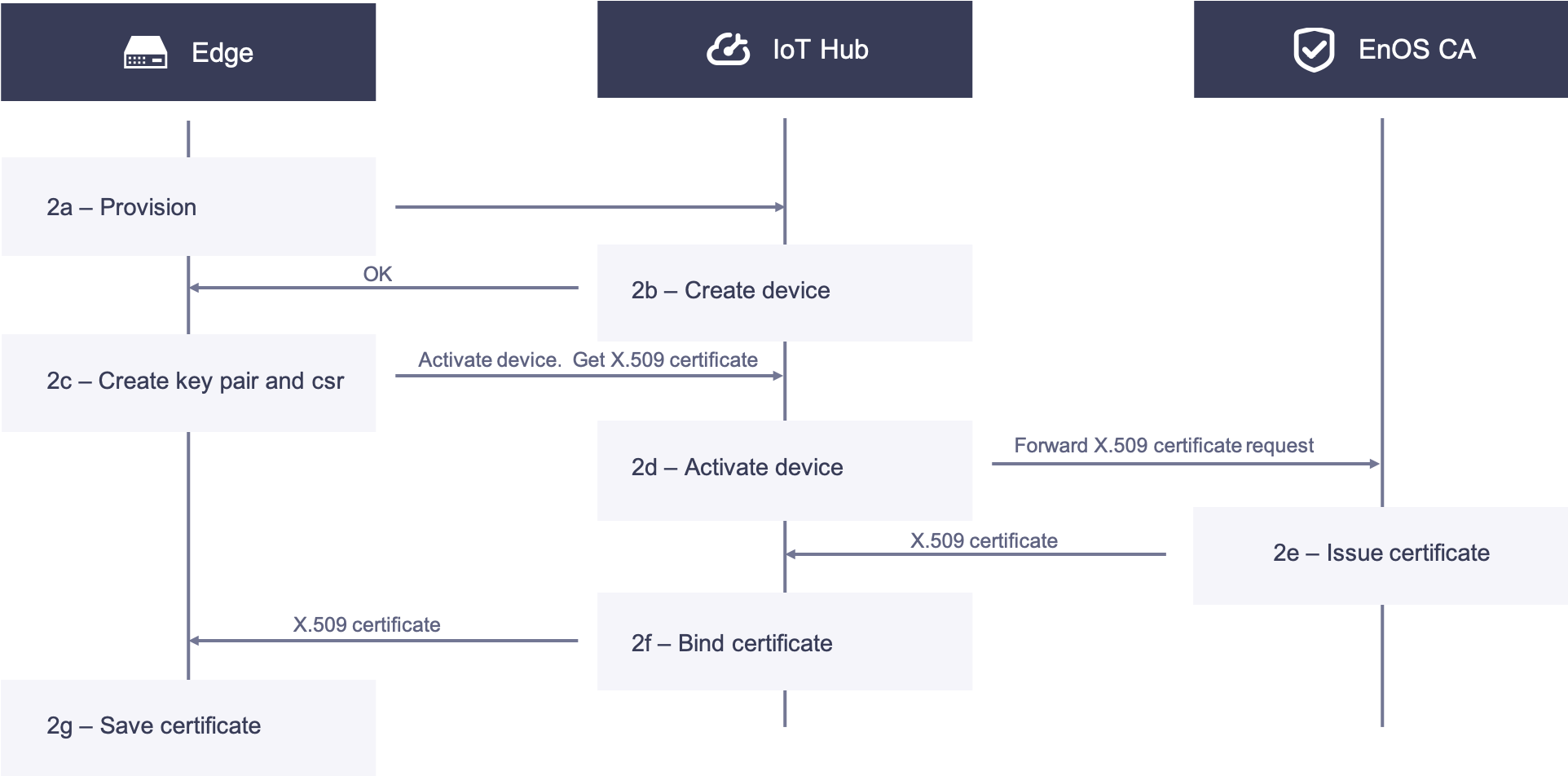
2a. Edge devices are pre-configured with the product key, product secret, and device serial number (SN) stored in themselves. When powered on and connected to the network, the Edge device reports its product key, product Secret, and serial number to EnOS Cloud for dynamic activation. EnOS Cloud returns the device secret to Edge if the authentication is successful.
2b. On EnOS Cloud, the serial number of the Edge device is used as the device key to create the Edge device instance. The device can be created either on the EnOS Management Console or by calling the API.
2c. The Edge receives a response from EnOS Cloud, creates the authentication keys and CSR, and calls the API to obtain its X.509 certificate. Meanwhile, the device authentication keys are used to log the device in to the cloud, and the device will be activated upon its first successful login.
2d. EnOS Cloud receives the CSR. After verifying its identity, the CSR is forwarded to the CA.
2e. The CA receives the CSR, issues the edge certificate and sends the certificate to EnOS Cloud.
2f. EnOS Cloud receives the issued X.509 certificate, binds it with the device ID, and then sends the edge certificate to the Edge.
2g. The edge receives the certificate and saves it locally in, for example, the Trusted Platform Module (TPM).
Communication Phase¶
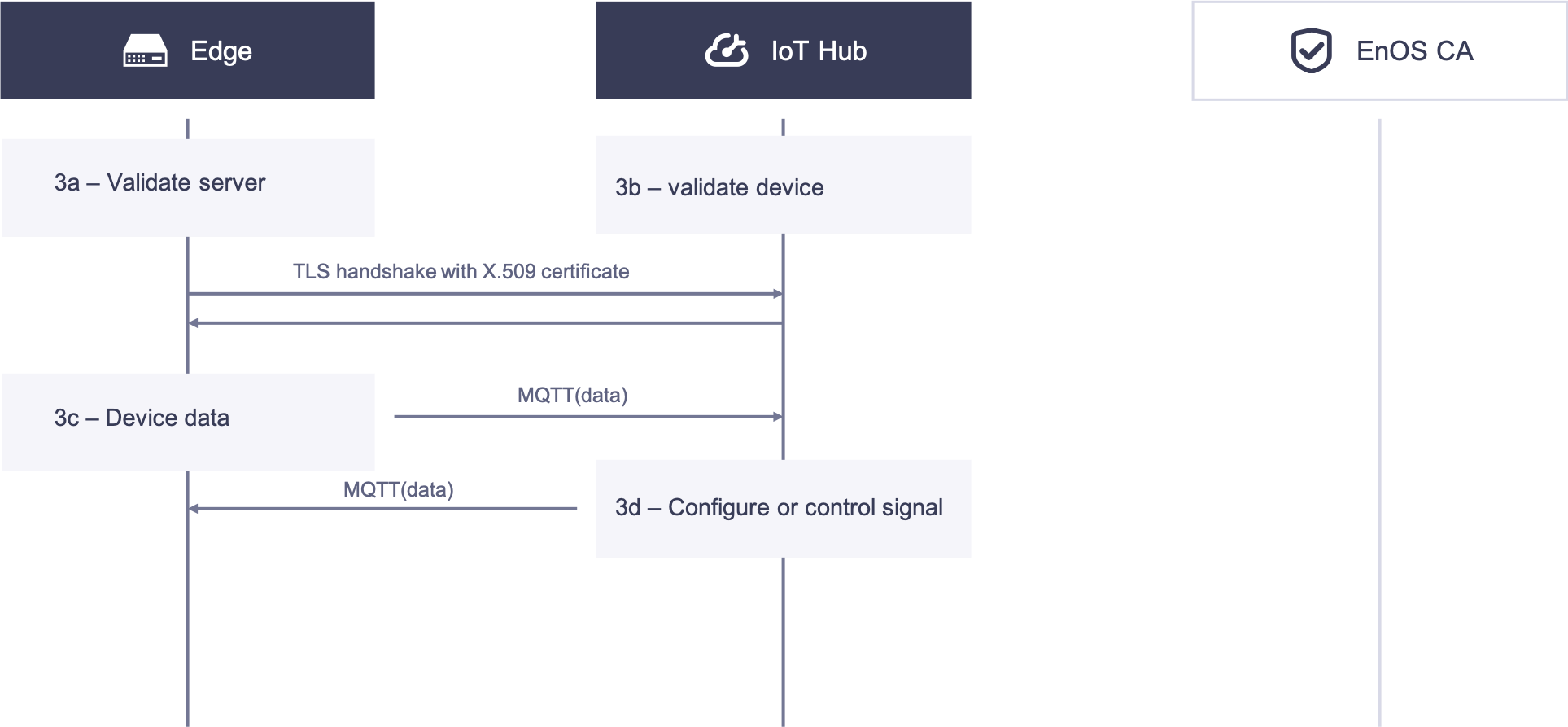
3a. EnOS Edge validates the certificate of EnOS Cloud.
3b. EnOS Cloud validates the certificate of EnOS Edge. When the TLS handshake in both steps 1 and 2 is successful, the TLS connection between EnOS Edge and IoT Hub is established.
3c. In the TLS channel, EnOS Edge transmits device telemetry information over the MQTT protocol.
3d. In the TLS channel, IoT Hub transmits configuration and control signals over the MQTT protocol.
Certificate Revocation¶
In some scenarios, the user needs to revoke the X.509 certificate granted to EnOS Edge. The following diagram illustrates the revocation process.
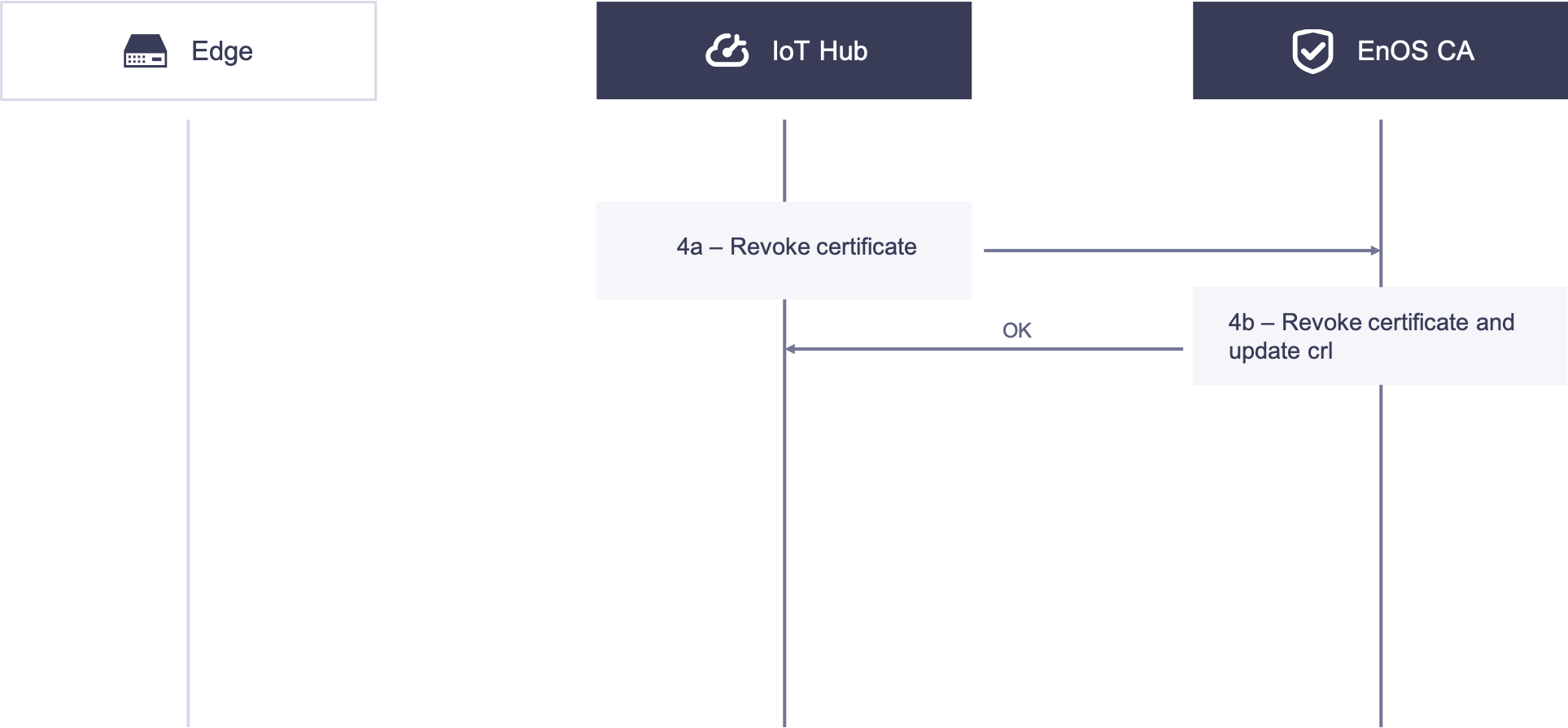
4a. IoT Hub calls the revocation API to request revocation of the X.509 certificate with the serial number on the EnOS Edge side from EnOS CA.
4b. The CA receives the revoke request from EnOS Cloud, authenticates the request, revokes the certificate, and updates the CRL.
Edge Security Best Practices¶
In the certificate-based authentication, consider using the following best practices:
Create a private key for EnOS Edge and keep it secret in a storage such as TPM.
Use TLS 1.2 when communicating with EnOS Cloud, and verify that the server certificate is valid.
Each Edge must have a unique public/private key pair.
The authentication keys used for authentication by EnOS Cloud should not be used for other purposes.
Revoke the authentication key when the Edge is reset.
Make sure your operating system on which the Edge runs is secured through certain mechanisms, for example, a firewall.
Ensure that you have a way to update the root certificates and CRL.
Ensure that the clock on the Edge is not tampered with.