CoAP-based Connection and Communication (Non-DTLS)¶
EnOS supports CoAP-based connection and communication. The CoAP protocol is suitable for resource-limited and low-power devices, especially for NB-IoT devices. This topic describes the CoAP-based connection process without DTLS.
The CoAP protocol specifications and limits used by CoAP connection without DTLS are the same as those with DTLS. See CoAP-based Connection.
Data Security¶
The device needs to have SHA-256 and AES-128 encryption capability to generate digital signature for authentication.
Connection Process¶
The process for connecting NB-IoT devices to EnOS via CoAP is shown as per the below.
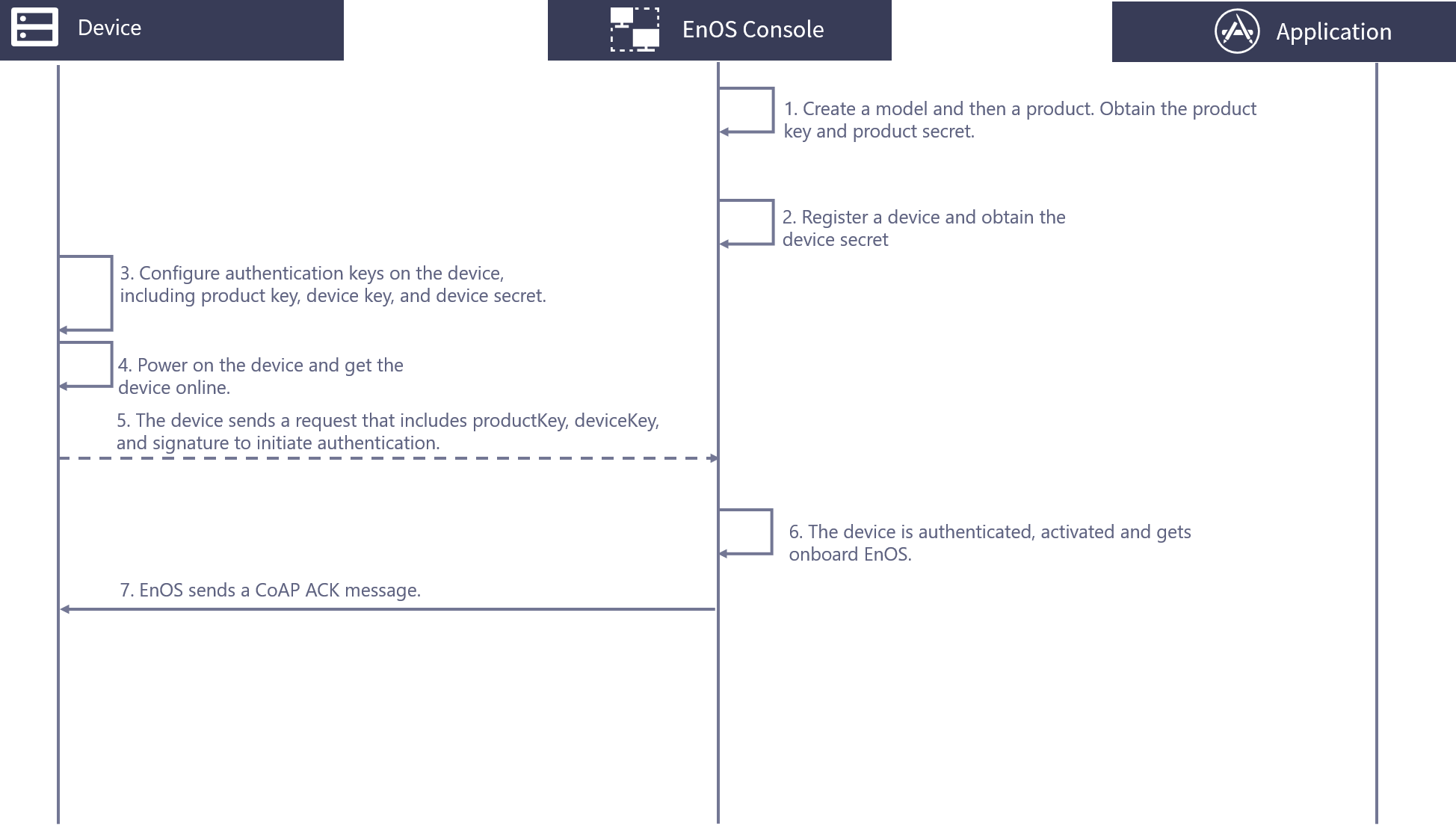
Obtain the product key and product secret by creating a model and then a related product in EnOS.
Create a device in EnOS and obtain its device secret.
Configure the authentication keys (productKey, deviceKey, and deviceSecret) on the device.
Power on the device and get the device online.
The device initiates an authentication request with the productKey, deviceKey, deviceSecret, and digital signature.
EnOS authenticates the device and the device gets activated.
EnOS sends an AKC message to the device to confirm that the device has been authenticated and is online.
Before You Start¶
Register the devices one by one and obtain their
productKey,deviceKey, anddeviceSecret. For information about how to register a device, see Registering a Device.Ensure that the device has SHA-256 encryption capabilities.
Connecting to the CoAP Server¶
The IP address of the CoAP server is coap-<hostname>, where the hostname is where EnOS is located. For example, if EnOS is located on abc.def.com, then the CoAP server address would be coap-abc.def.com.
Authentication and Connection¶
The device sends an authentication request in the following format.
POST /auth/${ProductKey}/${DeviceKey} Payload: { "secureMode": ${SecureMode}, "lifetime": ${Lifetime}, "sign": ${Sign} }
ProductKey: The product key used for authentication.
DeviceKey: The device key used for authentication. It should be unique within an organization (OU). You may use the IMEI of an NB-IoT device as its device key.
SecureMode: SecureMode is set as 2 CoAP connection without DTLS.
Lifetime: Used to determine the online status of device. A device would be determined offline if it does not exchange any message with EnOS within the period specified by Lifetime. Lifetime is counted in seconds and the value range is 30 to 86400.
Sign: The digital signature used for authentication.
A digital signature is generated using the following procedure:
1. Concatenate the following fields in the following order:
deviceKey${DeviceKey}lifetime${Lifetime}productKey${ProductKey}secureMode${secureMode}2. Attach
${DeviceSecret}to the end of the concatenated string:deviceKey${DeviceKey}lifetime${Lifetime}productKey${ProductKey}secureMode${secureMode}${DeviceSecret}3. Calculate the SHA-256 hash of the string generated in the previous step and capitalize all letters.
2. When the device is authenticated, EnOS will include a CoAP return code in the response. The format of the response is as follows:
Code: CoAP return code.