Scenario 2.2: Connect through edge gateway, Sub-devices dynamically registered¶
In this scenario, the edge calls the EnOS API to create the sub-devices dynamically.
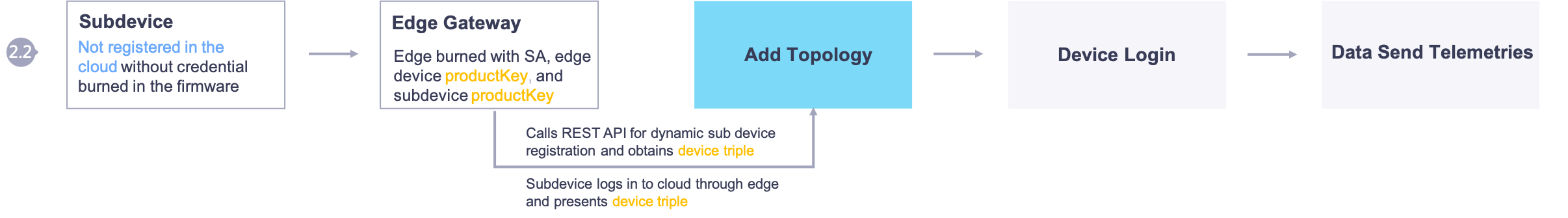
The following figure illustrates the message flow of connection scenario 2.2.
How to¶
In the EnOS Management Console, the edge developer registers an Edge application in the EnOS Cloud, and obtains the service account (SA) of the application: the
accessKeyandaccessSecret.The IoT engineer logs in to the EnOS Management Console and performs the following configurations in the customer’s organization:
Create an edge product and registers the edge device instance to obtain the edge device triple.
Create the product for the sub-devices to be connected through the edge and obtain the
productkey.
Burn the following information into the edge firmware during manufacturing:
The SA of the edge application, which will be used for obtaining access to the EnOS API.
The edge device triple issued by EnOS Cloud.
The
productkeyof the sub-device to be connected through the edge, and the identifier (orgId) of the organization that the device belongs to.
The EnOS Cloud performs the following authentication procedure when the edge device calls the REST APIs:
The edge uses the SA to gain access to the EnOS API. If the SA is incorrect, the edge will not be able to call the EnOS API and the authentication will fail.
The EnOS Cloud, based on the access policies defined in IAM, verifies the
orgIdandSAparameters carried in the edge connection request, and verifies whether the corresponding organization identified by theorgIdhas registered the edge application. If the edge application is not registered in the organization, the authentication will fail.The EnOS Cloud verifies the attribution between the two request parameters
orgIdandproductkey. If the product corresponding to theproductkeydoes not belong to the organization identified by theorgId, the verification will fail.
The EnOS Cloud performs authentication against the edge device.
By default, the edge enables the secret-based one-way authentication. The edge carries the device triple and connects to the cloud, where authentication will be performed based on the edge device triple, and the device is then allowed to log in if the authentication is successful.
The edge device will be activated upon its first login, and its status will be updated from Inactive to Online.
If the certificate-based two-way authentication is enabled, the process of certificate generation and distribution is as follows (using EnOS Edge as an example):
The EnOS Edge initiates a certificate request, which carries the certificate signing request (CSR), to EnOS IoT Hub.
The EnOS IoT Hub forwards the request to the EnOS Certificate Service.
The Certificate Service generates a certificate and returns it to the EnOS IoT Hub.
The EnOS IoT Hub records the certificate associated with the edge, and returns the certificate to the edge.
The IoT engineer configures the connection of sub-devices (e.g., inverters, fans, energy storage devices) that connects through the edge. The sub-devices can be registered via the following methods:
Dynamic registration: Creates the sub-device to be connected directly in the EnoS Edge Configuration Center and the Configuration Center calls the REST API of the IoT Hub to create the device in the EnOS Cloud.
Static registration: Creates the sub-device to be connected in the EnOS Management Console and then binds it in the EnOS Edge Configuration Center. The edge functions as a proxy and connects the sub-device to the EnOS Cloud.
Device data transmission
The edge is connected directly to the IoT Hub, and the sub-device is connected to the EnOS IoT Hub via the edge proxy.
Data is transmitted between the edge and the IoT Hub through the MQTT protocol.
If the certificate-based two-way authentication is enabled, the data transmitted between the edge and the IoT Hub is encrypted by the certificate.