Managing Service Accounts¶
A Service Account (SA) is a special EnOS account that is required by applications to access resources on EnOS via APIs. After an application is registered or purchased through in EnOS Management Console > Application Registration, a Service Account (i.e. AccessKey) is automatically obtained.
Service accounts is required when users perform the following operations through an application:
Accessing resources on EnOS via APIs
Consuming subscribed data by configuring data subscription tasks
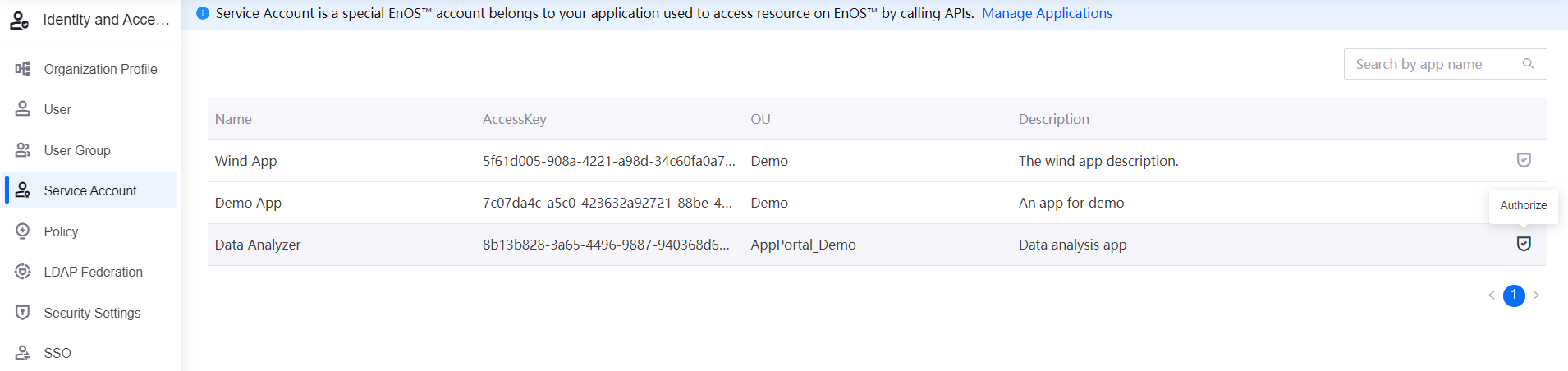
After obtaining a Service account, you can view all service accounts within the organization in Identity and Access Management > Service Account. Once the service account is authorized, the application has access to the corresponding resources on EnOS. After creating a key pair for the service account, you can use the key pair to decrypt the encrypted product secret and device secret obtained from the V2.4 version of the EnOS Connection Service APIs.
Prerequisites¶
You must be an OU administrator.
You have registered an application on the current OU, or have purchased an application from another OU.
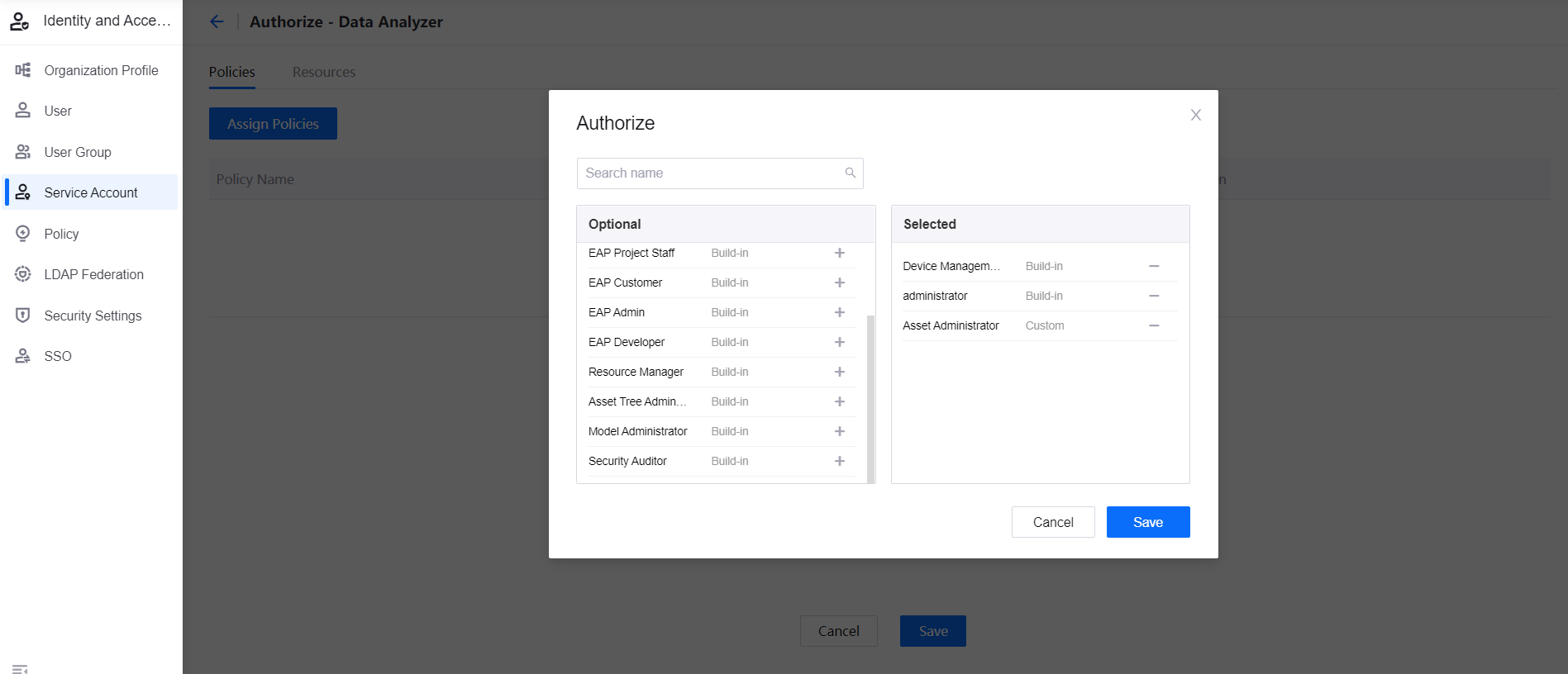
If you want to authorize with custom policies, ensure that the policy has been created. For more information, see Creating and Managing Policies.
Managing RSA Key Pairs¶
Note
This feature is only available if 2.4 Cumulative Update 1 has been applied to your environment. For more information, see 2.4 CU1.
A RSA key pair belongs to a service account, consisting of an RSA public key and an RSA private key. When you get the product secret or device secret via Connection Service V2.4 APIs, the return values will be encrypted, and you should use the RSA private key to decrypt. For more information about decryption, see Decrypting Product/Device Secret.
Only organization administrators of the organization to which the service account belongs have permission to create, update, and view it. There can only be one valid key pair for a service account at the same time.
Log in to the EnOS Management Console and select Identity and Access Management > Service Accounts from the navigation bar.
In the service account list, select the application for which you want to create a key pair and click Key Pair
 .
.(Optional)Set the Private Key Passphrase to encrypt the private key if required. The private key passphrase should be saved properly as it will no longer be displayed on the page. Leave blank if not required.
Click Create Key Pair to generate an RSA key pair.
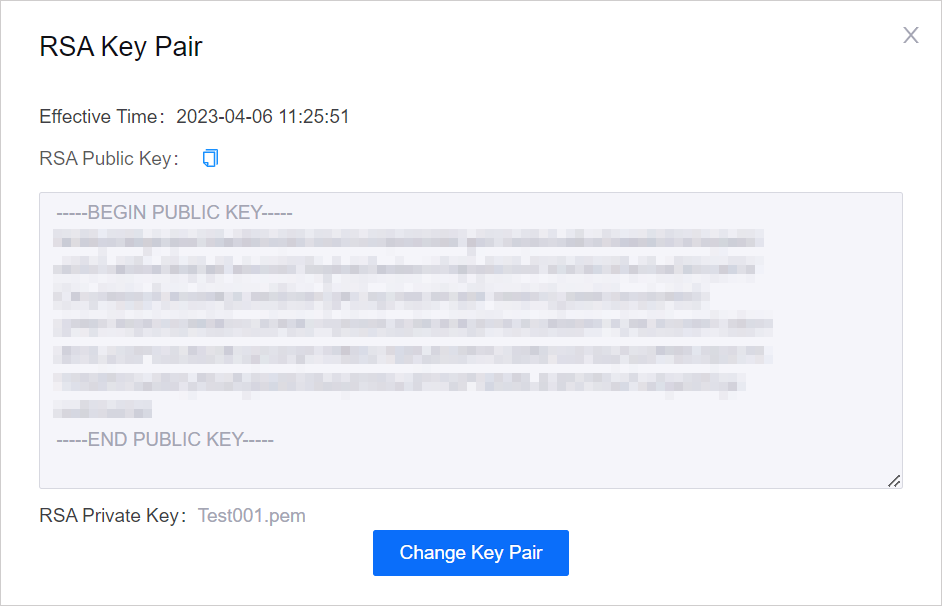
After creation, you can click Key Pair
 again to get the RSA public key and private key.
again to get the RSA public key and private key.Effective Time: the time when this RSA key pair is created or changed.
RSA Public Key: click Copy
 to copy the public key.
to copy the public key.RSA Private Key: click the file name (e.g. test001.pem) to download the encrypted private key file. The private key must be used in conjunction with the private key passphrase for decryption if you set the private key passphrase.
Change Key Pair: after changing the key pair, the original key pair will become invalid and cannot be viewed or downloaded on the page. Data encrypted with the original key pair can still be decrypted using the locally saved private key.