CoAP-based Connection¶
EnOS supports real-time data to be uploaded from a device to EnOS Cloud through the CoAP/UDP protocol. This feature provides secure connection and data management for massive devices.
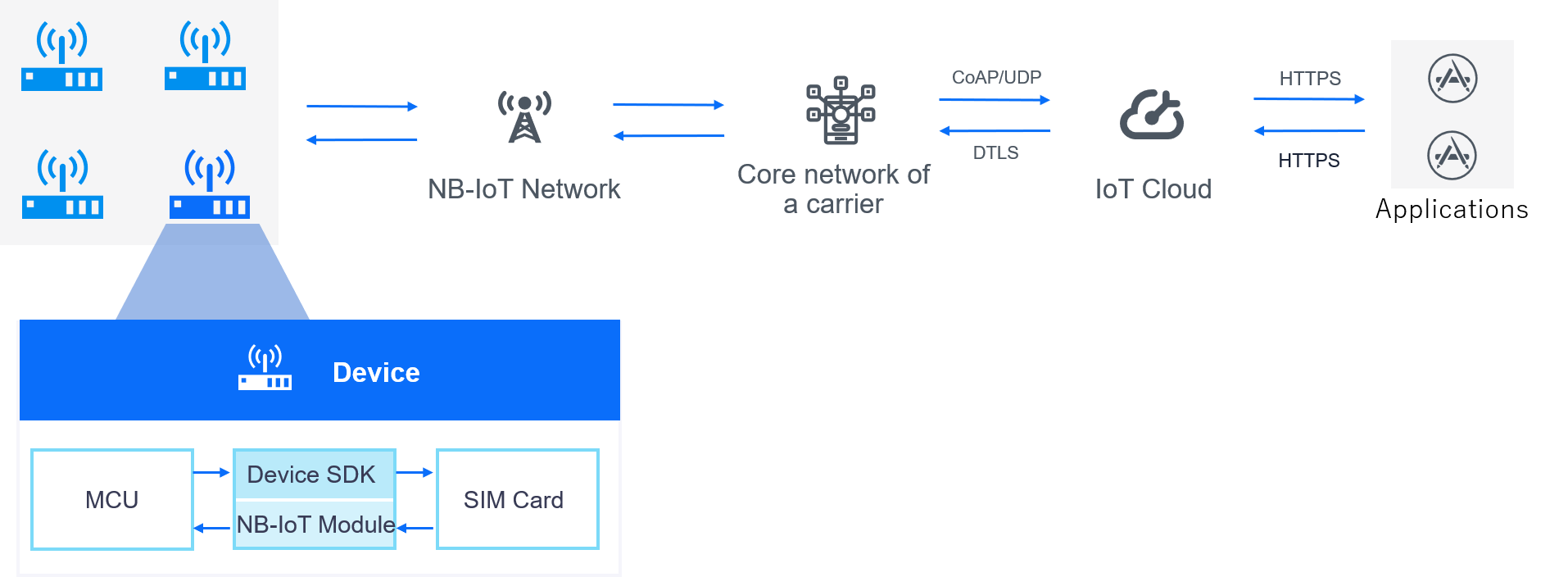
The process for connecting NB-IoT devices to EnOS is as follows.
Configure the authentication keys on the device, including the
ProductKey,DeviceKeyandDeviceSecret.The device connects to EnOS via the NB-IoT network provided by a carrier. The carrier is responsible for billing and the traffic data generated by devices and does not store any service data.
Developers can use EnOS open APIs to obtain data, modify measurement points, call device services, and export data into applications.
CoAP Protocol Specifications¶
The protocol supported by EnOS is the RFC 7252 Constrained Application Protocol. For details, see RFC 7252.
EnOS-specific Definitions¶
EnOS supports confirmable (CON) messages. The response to a request carried in a confirmable message is carried, or piggybacked, in the resulting acknowledgement (ACK) message.
EnOS supports the cacheability of CoAP prescribed in RFC 7252. Therefore, every new request uses a unique CoAP message ID and token.
EnOS also supports the block-wise transfers in the CoAP protocol. For more information, see RFC 7959.
DTLS Secure Channel¶
The device requests to connect to the specified CoAP server and then builds a secure channel. The procedure is as follows:
The device sends the DTLS handshake request to EnOS.
The device and EnOS negotiate PSK parameters as per the pre-defined algorithm.
The device sends the
pskidandlenparameters to EnOS for verification, and then builds a secure channel after a successful verification.
After a secure channel is established, the device initiates an authentication request. If encryption is adopted, this step can be combined with the DTLS handshake; otherwise, keys are required for authentication. Encrypted authentication methods include unique-certificate-per-device and unique-certificate-per-product authentication. Unique-certificate-per-product authentication requires that the device queries the device secret from EnOS before authentication.
EnOS uses DTLS v1.2 to ensure channel security. For more information, see RFC 6347.
Notes¶
Device connection based on CoAP reuses the topic specifications of MQTT.
EnOS does not support resource discovery or the Observe option [OBSERVE].
The size of a data packet that can be transmitted via CoAP depends on the size of MTU, which should be limited within 1KB.
Next Step¶
Refer to CoAP-based Device Connection to connect the device to EnOS and reuse the MQTT topic for data transmission with EnOS Cloud.