Offline Message Integration¶
Users can use the offline message integration feature to import the historical data from a third-party system into EnOS. Users can also set policies to process, store, and analyze the integrated data.
The offline message integration feature supports only one-way data transfer, i.e. from a third-party system to EnOS. Use this feature in the following scenarios:
Importing the historical device data from a third-party system.
Breakpoint resume for cached device data. For example, the measurement point data cached when a device is offline should be re-reported to the third-party system and then transferred to EnOS once the device gets online.
Protocol Supported¶
EnOS can import historical data and offline cached data in a third-party system by using the following protocols:
MQTT. For details about the MQTT topics used for offline message integration, request, and response formats, and parameter descriptions, see Offline Message Integration.
Process¶
The process of how the historical data and offline cached data of a third-party system are integrated into EnOS by using MQTT is shown as follows:
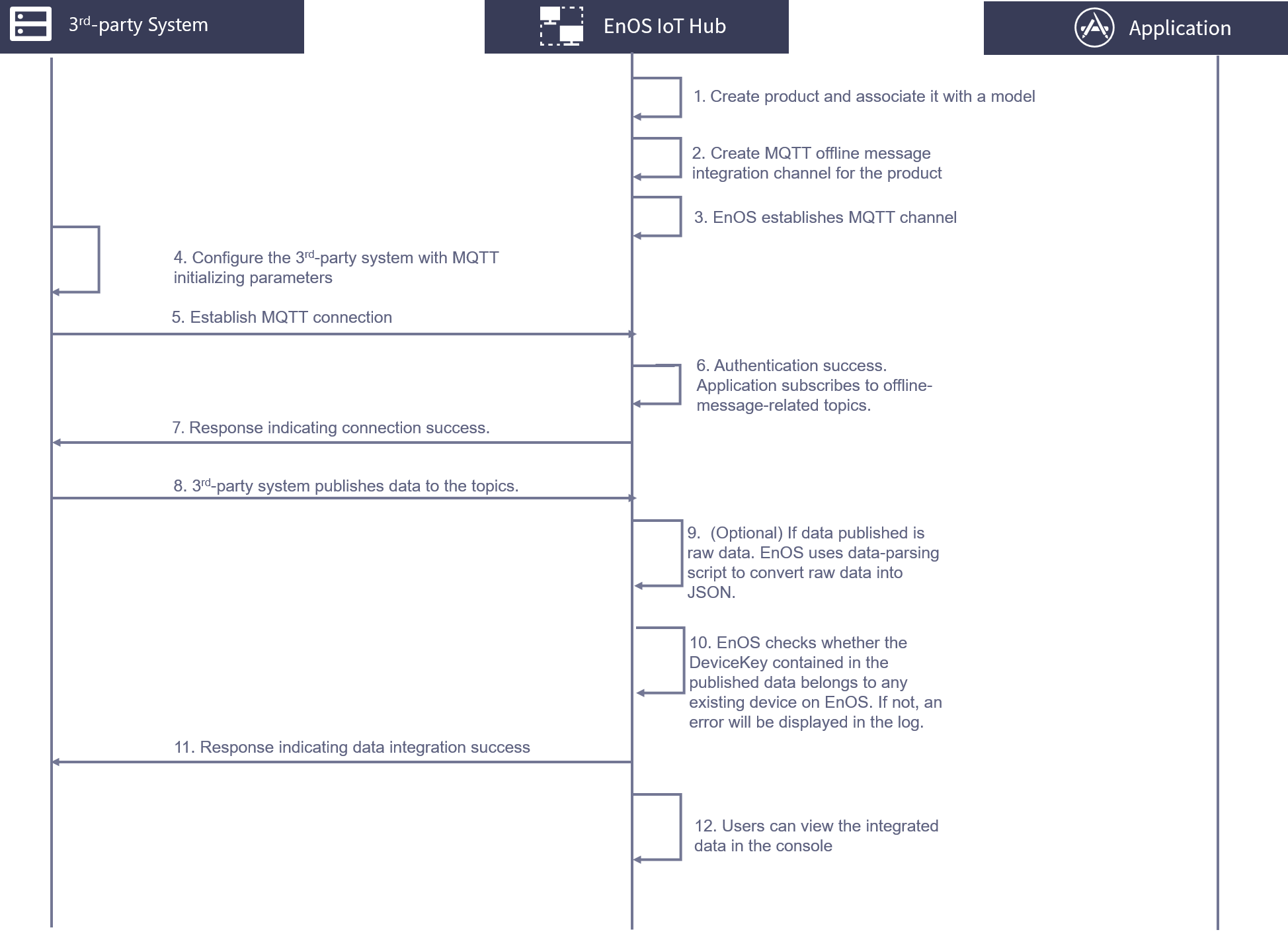
In EnOS, create a model and a product that uses the model, and then create a device that belongs to the product, whose data is to be integrated to EnOS.
On EnOS, create an MQTT message channel and obtain the following parameters:
Broker URL
ClientID
Username
Password
To obtain the parameters, on the EnOS Management Console, select Device Management > Message Integration, then select Details on the created message channel. You will find these parameters in Details.
EnOS will establish the MQTT channel.
On the third-party system, configure the parameters required to initialize the MQTT message channel, i.e. the MQTT parameters stated in the previous step.
The third-party system sends a request to set up connection.
The third-party system is authenticated. EnOS subscribes to the topics for offline message integration.
EnOS sends a reponse indicating the authentication is successful.
The third-party system publishes the offline messages to specified MQTT topics. An independent broker is responsible for data publishing and subcription beteen the third-party system and EnOS rather than reusing the existing broker that is used for real-time data publishing and subscription.
(Optional) If the raw data of a device (e.g. binary data) is passed through by the third-party system, EnOS will use the data parsing script to convert the raw data into the EnOS-defined JSON format.
EnOS detects the deviceKey carried in the historical messaged reported by the third-party system.
If the user has not registered the device on EnOS, EnOS will report an error in the log and the historical data cannot be integrated.
If the deviceKey exists, the historical data will be saved.
EnOS sends a response to the third-party system indicating that the integration is successful.
The user can now view the historical message integrated on EnOS.
Note
To view the message log for the channel, select Device Management > Message Integration. Then select the message channel and click Details for the log. The message log includes the following information:
Channel connection information such as MQTT connection/disconnection records.
Payload transmission log.
Error log such as JSON format verification failure or script invocation error.
For more information about creating offline message channels, see Integrating Device Data from Offline Channel.
Offline Message Usage¶
After the historical messages of the third-party system are integrated into EnOS, applications can use the data by calling the EnOS APIs. For more information, see About EnOS API.
In addition, the user can subscribe to offline message data streams on EnOS, where the offline data are published to the corresponding Kafka topics through the rule engine and be available for subscription by data asset management functions.